Bonanza Offer FLAT 20% off & $20 sign up bonus Order Now
Technological advancements have made the life of human more easily than in previous days it was. In spite of these advantages of technology, the chances of data theft, malfunctioning of system has not only increased but also these are most common threats to human. Identity Access Management is one of the technological advancements those protect the system or applications from these threats (Everett 2011, p.12). It is also known as IAM. This term is defined as: it is on security and business discipline that allows the right individual the right access at the right time with a right purpose behind his access.
In this report, the impact of IAM in human is life discussed with respect to Heaclscope organization situated in Australia. This report will be explaining importance of IAM with its technological implementation.
IAM is known as Internet Access Management. This term has introduced in to the scenario to realize several business benefits (Fuchs &Pernul 2013, p. 89). These benefits are as follows: cost saving, control of management, operational efficiency, and most importantly growth of business for E- Commerce. Every organizationhasto manage their data distributed among external and internal application systems. In addition to this these organization have to provide these data for growing identity to both outside and inside the organization ("PRIAM: Privacy Preserving Identity and Access Management Scheme in Cloud" 2014, p.283). This aspect introduces that these data should not contain any malware or systemcannot be corrupted due to the transfer of data. The security concerns are always on high priority in this case.
IAM is generally comprised of the product, people and process for managing identities and access to the resources of the enterprises. Functionality of the IAM framework should require correct data from organizational resources (Khansa & Liginlal 2012, p. 79). IAM components can be classified into four categories: Authentication, Authorization, User management, central user repository.
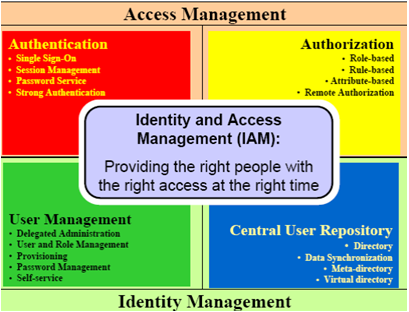
Figure 1: Identity and Access Management
(Source: Thananusak& Ansari 2015, p.16390)
Authentication: Authentication module of IAM provides sufficient credentials to the user for accessing the application system or any specific resource(Sharman, Smith & Gupta 2012, p. 47). Once the user is authenticated they will stay connected with the system until they logs out.
Authorization: Authorization module of IAM provides the user legal and authorized access to the application or system. This module checks if the user is permitted or not to access the application or resource.
User management: This module deals with password management, group management and user management. This module defines the set of administrative functions thatshould be centralized for providing the user facility (Lodwick 2014, p. 112). This includes creation of user identity, propagation and maintenance of user of identity.
Central user repository: this module of IAM stores and delivers the information related to identity to other system and applications (Maclean 2015, p.57). This presents a logical view of identities within an organization. It provides 2-way data synchronization system for the better of the concerned system within organization.
Importance of IAMAccording to the security concerns identity access management have great impact on technological world. These impacts can be explained with the help of its benefits. IAM is generally used to secure the business process like data transfer, online activities using identity management (Schorer 2014, p. 327). A user misuses the data and identity several times. Identity and access management prevent this kind of malfunctioning. Following are the importance of IAM in business world:
| Importances | Description |
| Identity and data collection | Detail information about the users are collected only with the help of IAM. |
| Data analytics | Overview of the application or system is designed with the help of data analytics. |
| Access reviews | Detailed information about the accessing process as well as individuals is informed by access reviews (Silberzahn & Kilduff 2013, p. 16388). |
| Policy management | Policies are managed by IAM. |
| Role management | Capabilities related to policies and roles are managed by IAM. |
| Access request management | Requests from the user can be managed by IAM. |
| Provisioning | IAM prevents every malfunctioning and malwares that is detected. |
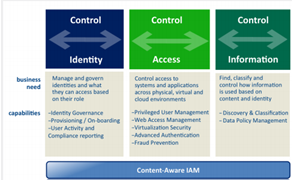
Figure 2: Control of IAM
(Source:Lodwick 2014, p.113)
Identity and data collection: IAM collects all the data from the identity store, account and transfer it to the application, roles and system by centralizing them in a unified way.
Data analytics: Visibility provided across the identity store includes: dashboard, analysis of identity related documents and details in the store (Thananusak & Ansari 2015, p. 16390).
Access review: Accessing details in business are very important. IAM check these details and transfer it to the identity store for collecting and managing the data. This involves review of application owners.
Policy management: There are several policies within a concerned business. This involves management of these policies (Thomas & Sekaran 2014, p. 125). IAM do this for the business practices.
Role management: The ability to demonstrate policies and to detect the violation IAM is selected. It initiates the remediation process.
Access request management: Several requests from the users are not only collected but also handled by IAM (Uddin & Preston 2015, p. 154).
Provisioning: IAM protects all kind of data as well as identities stored in the identity store.
There are several developmental features of IAM in contrast with the organizational needs of Healthscope. These developments are specified by services provided by this aspect. These services are explained as follows:
| Services | Functionality |
| Authentication of subject | · Identity directory service · Movers, joiners and leaver service · Management of user identities · Federation related to identity · Yellow pages/white pages · Strong management of authentication |
| Access resources | · Profile management, management of roles and functions · Admin and user’s delegated services · Management workflows · Provisioning of user accounts · Physical access management · Enforcement of application policies · Single sign in facility · Real time control and access to application and resources |
| Monitoring | · Audits and reporting · Attestations · Event and alarm management |
Identity access management system can manage the authentication and entitlement of the user’s access to the application and resources. It determines the aspects that the user can easily access and experience (Thomas & Sekaran 2014, p. 125). It is totally based on the user context. This decides the dos and don’ts of the user. These services provided by IAM can allow the user to check if their access is safe or not. Security issues re handled on the top priority (Everett 2011, p. 12). In spite of the one IAM system hasto operate many systems to regulate several accesses.This management includes: management of lifecycle of the user identity, resources and accounts. Otherwise every time the user may change their identity toaccess the application or resource which is not right and safe for the system. To regulate these issues IAM conveys some services: Authentication of subject, Access resources and Monitoring of identities (Fuchs & Pernul 2013, p. 89). All of these services provide the organization as well as the user to securely handle their data and identities.
There are several technologies that can be used for IAM for authorizing an authenticating the identities. These technologies are as follows. These technologies can be used by Healthscope for improvisation.
Directory services: Directory services considered of the mapping of name of the networks with the particular net address. The system contains a server that provides directory service considering each network as an individual objects (Khansa & Liginlal 2012, p. 79). Information form these objects got flowed through IAM. Healthscope can easily operate their numerous numbers of applications that are being operatedwithin their organization.
Digital identities: This is nothing but an identity utilized by the computers in the digital form. The agents involved within this technology may be person or system. This technology teaches the computer to how to treat the external agents (Lodwick 2014, p. 113). The information stored within this system allows the user to get knowledge about the happened interactions between external and internal agents.
Security token services: security token services are nothing but software that checks the validation of the user or more specifically the identity (Silberzahn & Kilduff 2013, p. 16388). The application does not authenticate the identity it sends the identity to the STS, that checks if the identity is validated or not. Token is packed claims that are stored with in the information.
OpenID: This is “open standard and decentralized authentication protocol”. This authenticates the user by co-operating sites (Maclean 2015, p. 57). This allows the third party to provide their ad hoc login ids. This application has control over several websites that allows the user to be authorized with single passwords and ids.
Identity and Access Management is one of the most innovative trends in contemporary times. This authenticates and authorizes the user to protect their identity from several threats and malfunctions. It has great impact on business needs. According to the context of IAM it allows the user the right access at the right time with right reason behind their access. This aspect is also maintained in case of organizational demands. In this report the impact of IAM is described with respect to Healthscope organization situated in Australia. This organization wants to implement IAM technologies within their organization for improving their system and work culture. For this purpose this report is presenting impacts of IAM to the CISO of Healthscope. In addition to this importance and applications of IAM is discussed in this report.
"PRIAM: Privacy Preserving Identity and Access Management Scheme in Cloud" 2014, vol. 8, no. 1, pp. 282-304.
Everett, C 2011, "Identity and Access Management: the second wave", in , Computer Fraud & Security, vol. 2011, no. 5, pp. 11-13.
Fuchs, L &Pernul, G 2013, "Qualitätssicherungim Identity- und Access Management", in , HMD, vol. 50, no. 1, pp. 88-97.
Khansa, L &Liginlal, D 2012, "Regulatory Influence and the Imperative of Innovation in Identity and Access Management", in , Information Resources Management Journal, vol. 25, no. 3, pp. 78-97.
Lodwick, D 2014, "Access and Identity Management for Libraries: Controlling Access to Online Information", in , Technical Services Quarterly, vol. 32, no. 1, pp. 112-113.
Maclean, L 2015, "Access and identity management for libraries: Controlling access to online information", in , The Australian Library Journal, vol. 64, no. 1, pp. 57-57.
Schorer, C 2014, "A Review of “Access and Identity Management for Libraries: Controlling Access to Online Information”", in , Journal of Access Services, vol. 11, no. 4, pp. 327-328.
Sharman, R, Smith, S & Gupta, M 2012, Digital identity and access management, Information Science Reference, Hershey, PA, pp. 45-70.
Silberzahn, R &Kilduff, M 2013, ""The Hidden Difference - Identity Status, Access of Knowledge and the Generation of New Ideas"", in , Academy of Management Proceedings, vol. 2013, no. 1, pp. 16388-16388.
Thananusak, T & Ansari, S 2015, "Identity Alignment in the Inter-organisational Relationship: The Case of Open Access", in , Academy of Management Proceedings, vol. 2015, no. 1, pp. 16390-16390.
Thomas, M &Sekaran, K 2014, "Agent-based approach for identity and access management in the inter-cloud environments", in , International Journal of Trust Management in Computing and Communications, vol. 2, no. 2, p. 125.
Uddin, M & Preston, D 2015, "Systematic Review of Identity Access Management in Information Security", in , JACN, vol. 3, no. 2, pp. 150-156.
MyAssignmentHelp.co.uk is not a new name in the field of essay writing services. For almost a decade MyAssignmentHelp.co.uk has provided the students in the UK with the essential essay help whenever requested and still continues to do so with the same enthusiasm. In fact, their custom essay writing help is specially designed to serve the specific requirements of every student in the country.
Upload your Assignment and improve Your Grade
Boost Grades