Bonanza Offer FLAT 20% off & $20 sign up bonus Order Now
| Repeater | Switch | Router |
| Repeaters are found in switches and hub | A switch is a device which has multiple ports | “A router is similar to switch in functionality. It also works by forwarding data using the correspondent IP address” (Krishnan, 2011). This helps in using different protocols. |
| The working of the repeater is to clean, amplification, and resending of the signals | Error checking can be performed by the switch by forwarding data
| It is used for providing connection to the LAN and WAN and also update the routing table which is used for routing the data packets |
| Regeneration of the signal can be done by using the repeater | Switches are highly efficient in sending good packets only to the destination and rejects the error prone packets to forward it further | The division of broadcast domain can be done by using routers |
| It is mainly used at physical layer | “Switches provide support to layer 2 and 3. The layer 2 is based on MAC address whereas layer 3 depends on the IP address” (Michael, 2015) | Routers is mainly used in the network layer |
| Bit by bit copy the signal and produce the original strength of the signal | Switch forward messages based on hardware | Router forward messages based on software |
| It does not support WAN technologies | Switch does not support WAN technologies | Router support WAN technologies |
Switches are more expensive than repeater because Switches provide support to layer 2 and 3. The layer 2 is based on MAC address whereas layer 3 depends on the IP address whereas repeater provides support to layer 1 that is physical layer.
2:
The total number of addresses is 128. /25 subnets are used for 128 addresses that is 255.255.255.128.
a) The first group is having 200 business of medium size.
150.80.0.0 / 25 is categorized as subnet 1
150.80.0.128 / 25 is categorized as subnet 2
150.80.1.0 / 25………..150.80.1.128 / 25 is categorized as subnet 3
This will continue for 100 subnets that is from 150.80.99.128 / 25 to 150.80.99.255. The next correspondent address will be 150.80.100.0.
150.80.100.16 / 28 is categorized as subnet 1
150.80.100.240 / 28 is categorized as subnet 16
…….150.80.124.240 / 28 is categorized as subnet 400
The next correspondent address will be 150.80.125.0
150.80.125.0 / 30 is categorized as subnet 1
150.80.125.4 / 30 is categorized as subnet 2
150.80.125.252 / 30 is categorized as subnet 64
150.80.155.252 / 30 is categorized as subnet 1984
31 * 64 = 1984
150.80.125.156.0 / 30 is categorized as subnet 1985
150.80.125.155.60 / 30 is categorized as subnet 2000
The next correspondent address will be 150.80.156.64
40000 addresses have been used out of 65536 addresses. The number of available addresses are 25536
3: In the given diagram, assuming that the interfaces of all routers are operational and the configuration has been done correctly. The default configured route of R1 will be more critical than R2 because any packet which is designed for the complete network which is not referenced in the routing table for the R2 router will directly affect the R1 router. The sending of the packet back from R1 to R2 will takes place and the occurrence of routing loop starts.4: Comparing between distance vectors routing with link state routing is given below:
Distance Vector Routing: This type of routing uses distance vector routing algorithm for example, “Bellman Ford routing algorithm which is based on direction and the distance between any links in the interconnected network for determining the best route” (Gordon, 2008). The information is send periodically from one router to another neighboring router. The cost is correspondent to the hop count. The problem which is incurred in distance vector routing is of step by step updating the network. “The high bandwidth is required for distance vector routing because every router sends his complete routing table to its neighboring router at regular interval of time” (Shukla, 2014).
The description is summarized below:
For the calculation of shortest path it make use of bellman ford routing algorithm
The information is send periodically from one router to another neighboring router.
The distance node is reached by calculating the hop count
It is a type of decentralized routing algorithm
The example of the distance vector routing algorithm is RIP
It makes lesser utilization of CPU and memory space.
“The problem which is incurred in distance vector routing is of step by step updating the network” (Singh, 2011).
The high bandwidth is required for distance vector routing
Every router sends his complete routing table to its neighboring router at regular interval of time.
In this routing algorithm, every router is comprised of building the complete topology for the entire network connection. In this every router consist of the same information. In link state routing algorithm router send the information to the router which is related to the change in the structure of the topology for the network. The Shortest path first is another name for link state routing protocol. “The examples of the link state routing protocols are BGP, OSPF, and EGP” (Brightwell, 2013). In this algorithm, hierarchical structure is developed which requires more power in processing and updating the data base. The database carries the details of the router which are used in constructing the network.
For the calculation of shortest path it makes use of Dijkstras algorithm
Every router is comprised of building the complete topology for the entire network connection.
The same information is contained in every router
The Shortest path first is another name for link state routing protocol.
It requires more power in processing and updating the data base.
The database carries the details of the router which are used in constructing the network
5: ICMP: Internet control message protocol is a protocol which is used for error reporting of the network devices for example, routers which are used for generating the error messages for the source IP address and preventing the delivery of IP packet over the network. ICMP is used for creating and sending the messages to the source IP address which indicates the gateway to the internet by making use of router, host, or service for delivery of the packet. The network devices which are based on internet protocol are capable of sending, receiving, and processing of ICMP messages. This protocol is mainly used by the routers, hosts, or other intermediary devices which are used for communicating error messages or for providing updated information to other routers. The transmission of ICMP messages takes place in the form of datagram which consist of ICMP data in the portion of IP data. It is used for executing the denial of service attacks by sending the larger number of bytes in IP packet by making use of IP protocol. The function provided by the ICMP protocol can be summarized as announcement of the network error, announcement of the network congestion, assessment in doing trouble shooting, announcement of the timeout. “The ICMP protocol is responsible for detecting the error occurred in the network and sends ICMP reports” (Buhalis, 2012). The network devices which are based on internet protocol are capable of sending, receiving, and processing of ICMP messages.The IP protocol model is comprised of five layers which are categorized as Application layer, transport layer, internet layer, data link layer and physical network. The ICMP protocol is responsible for detecting the error occurred in the network and sends ICMP reports on dropping of the packets arrived at faster rate than processing, in case failure connection of the connection when the host cannot reached to the destination, and in the case of redirection when the host sending information to another router. The ICMP uses ping command which contains relevant information about the commands of operating system.
The tools based on ICMP protocols: The name of the tools based on ICMP protocols are ping and trace-route. These are used for sending probe packet to the host and also help in measuring the loss by observing the response of the packet.
Ping: “The ping is used for sending ICMP packet by type 8 echo request to the destination address” (David, 2011). In this the reply is asked by the destination address. For the generation of the reply, swapping of the source and the destination address takes place. After receiving the packet comparison of time correspondent to echo request is carried out. In the process, the round trip time of the packet is calculated.
Trace-route: The utilization of the trace-re is similar to ping. The series of ping packets are sends with the starting time named as Time to live. The value of time to live is equal to 1 and the value get increased by one with the series of the subsequent packet. The decrement in the time to live takes place when it crosses the routers. When the value of time to live become zero, the further transmission of the packet will not takes place. The packet is sent back to the ICMP message known as Time exceeded. The first router which is discovered in the path from source to destination will be marked as “Time Exceeded” ICMP message. This also helps in the identification of the IP address. The blocking of the second packet will be take place at second router and similarly others.
In using this routing protocol two principle problems which are encountered are loss asymmetry and ICMP filtering.
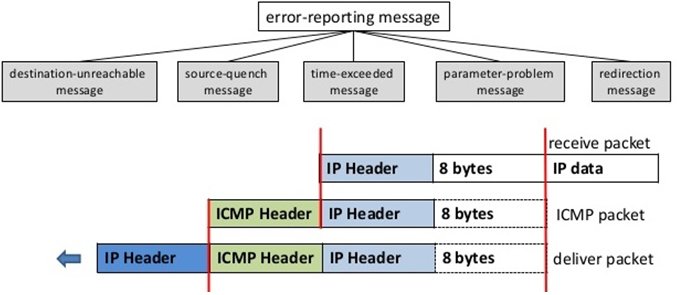
The purpose of including the IP header and first 8 bytes of datagram data in error reporting ICMP messages is that the beginning of the payload contains the encapsulation of the header of the higher layer. The ICMP message contains either the UDP header or TCP header (first eight byte of the header). The message includes the details of host and the destination port numbers.
Krishnan, K. (2011). Internet Control Message Protocol (ICMP) (1st ed.). Retrieved from http://www4.ncsu.edu/~kksivara/sfwr4c03/lectures/se4c03lecture5.pdf
Michael, B. (2015). IP Addressing and Subnetting for New Users (1st ed.). Retrieved from http://www.cisco.com/c/en/us/support/docs/ip/routing-information-protocol-rip/13788-3.html
Gordon, S. (2008). A short module on Internet control message protocol (1st ed.). Retrieved from http://www.cs.virginia.edu/~cs458/slides/module08-icmp.pdf
Shukla, P. (2014). Comparative Analysis of Distance Vector and link state routing protocol (1st ed.). Retrieved from http://www.ijircce.com/upload/2015/october/59_Comparative.pdf
Singh, F. (2011). Performance analysis of distance vector and link state dynamic protocol (1st ed.). Retrieved from http://www.ijcstjournal.org/volume-3/issue-4/IJCST-V3I4P4.pdf
Brightwell, T. (2013). Traffic regulators: Network interfaces, hub, switches, bridges, routers, and firewall (1st ed.). Retrieved from http://gonda.nic.in/swangonda/pdf/networkdevice.pdf
Buhalis, K. (2012). Network component and devices (1st ed.). Retrieved from http://gonda.nic.in/swangonda/pdf/0789732556.pdf
David, T. (2011). Connectivity and Interconnectivity devices (1st ed.). Retrieved from http://www.cs.princeton.edu/courses/archive/spr09/cos461/docs/lec09-switches.pdfMyAssignmenthelp.co.uk is a name in assignment writing services that students trust. We offer our assignment writing services for a wide variety of assignment including essays, dissertations, case studies and more. Students can place their order with us anytime as we function 24x7, and get their copies at unbeatable prices. We guarantee that all of our solutions are plagiarism-free.
Upload your Assignment and improve Your Grade
Boost Grades