Bonanza Offer FLAT 20% off & $20 sign up bonus Order Now
TCS in the last few decades had become a global leader in providing technology services and consultation. It is established in 50 countries covering all over the world. It provides strategies for the digital transformation of the companies. In today’s era, every business is transforming from traditional client-server model to internet based applications. In the designing of the application, the unrestricted accessing of the website should be provided to the users. This is the main cause of threat of attack. “The hackers usually take the advantage of global accessing and gain the unauthorized access over the website information”( Singh, 2013). The normal procedure of the application can be disturbed. When dealing with the security concern of the organization, the preventive steps should be taken of two things which can be categorized as violation of information and unauthorized accessing of the information. The security associated with the application is comprised of four things which are named as privacy, authorization, integration, non repudiation. The privacy of the data should be provided to the users which mean providing protection to the confidential data from unauthorized access.” Authentication is the process of identifying the users. Only authorized persons should be given permission of reading, writing, and deleting the information” (Muruthy, 2008). The non repudiation compels the user to admit that they have done the transaction of information.
Mission:
The TCS is working in providing the technological services and consultation to variety of companies. In this paper, we will focus on the security challenges which are faced by the organization and solution and remedies provided by the company to overcome the security issues.
Values:
“The TCS focuses on the change management, integration, individual values, knowledge sharing and excellence” (Buhalis, 2014).
“The testing of the security helps in providing verification and validation that the security requirement of the application is fulfilled or not” (Butt, 2014). It also helps in the identification of the vulnerabilities which are associated with the application.
For checking the security issues of an application, it is necessary to list out the requirements which are needed by the application. “Since the security issues are raised with the advanced development of the application it is necessary to provide fine grained security to the application” (Dewanjee, 2010). The first level of security checking focuses on the users of the application. To check the security issues it is necessary to list out all the security issues which are associated with an application. The next step is to identify the sub parameters of the issues. All the sub parameters should be tested separately. The last step is to provide priority to the security issues associated with the sub parameters. “When dealing with the security concern of the organization, the preventive steps should be taken of two things which can be categorized as violation of information and unauthorized accessing of the information” (Devi, 2013). “Firstly, the collection of requirement of security issues, secondly analyzing and designing the scenarios for testing the security, thirdly testing after implementation, and lastly interpretation of the test report” (Bhatia, 2013).
| No. | Parameters | Dimension | Dimension | Dimension | Dimension | Dimension | Priority |
| 1 | Authentication | No authentication | Based on password | Based on smart card and PIN | Based on Biometric | Based on Digital certificates | 9 |
| 2 | Authorization | No authorization | Based on role | Based on User | Based on electronic signature | Based on role and user | 8 |
| 3 | Access Control | No access control | Based on context | Based on user | Based on role | All the three | 6 |
| 4 | Non repudiation | No non repudiation | Based on digital signature | Based on encryption and digital signature | - | - | 4 |
| 5 | Audit control | No audit control | Based on firewalls and VPN logs | Based on custom based logs | Based on employ managed security services | - | 6 |
Infosys is the multinational company which helps in managing risks associated with the organizations, give assurance about the regulatory compliance, prepares strategies for empowering the risk, works on achieving cyber resilience, and helps in recovery from the security issues which are encountered within the organization. “From the survey, it was determined that the track record of TCS is impressive in giving solution to the organization all over the world” (Turn, 2009). The processes which are robust in nature help in providing security services to more than 6000 security associates. The main focus of the Infosys is to develop centers for the management of vulnerability, solution for cyber security, forensic labs, and many others. The company provides aligned solution with the requirement of the client organization. “The consultants of TCS organization are categorized as centers for security operations and the organization for the vulnerability management” (Kunnauthur, 2008).
TCS is working in the direction of maintaining the quality management system. “The quality management system of the organization should be associated with the features like vibrant, process driven strategies, integration, people oriented strategies, and focusing on customer demand” (NelsonHall, 2015). The number of technologies which are used by the organization to measure and monitor the security issues, management of the log, incident management, and the services provided for remedies. It is also associated with the number of accelerators for example dashboard, reporting templates and threat intelligence. “The services which are provided by the organization in focus network security are like network intrusion detection and prevention, managing the firewall to restrict the entrance of the intrusion, providing remote accessing security, IPS management, the gateway of the email and web should be secured, and controlling of the network access from the unauthorized users” (Oshri, 2011). This type of security mechanism is working on managing the anti-virus, host intrusion prevention, protection from monitoring and integration, management of application, advancement in the technologies used for detecting the threats, protection from mobilization of the enterprise, and the security mechanism for hypervisor. This type of management system provides services for the complete development of the application, network platform and mobile devices. The services offers for managing the vulnerabilities are the collection of managing the vulnerabilities throughout the development of the application, services offered for security, and the threat intelligence security service. “Data security and privacy is the collection of encryption technologies or procedures, prevention from the data leakage, and services offered for key management” (Kulandaivel, 2013). The services for assessment, development of design, and implementation are also provided by the organization. The organization provides solutions which are the combination of evaluation of the solution and its road mapping. It works on developing the program and technologies which works on overcoming security issues which are associated with the organization. The services provided by the government and the identity federation are also accessed by the organization. It works on developing the lifecycle management for overcoming the security issues.
The security team of the TCS organization works in providing the automation to the programs and processes which are designed for monitoring the deviation which occurs in the management of risk, governance, and the requirement associated with the resilience of the organization.
The metric stream and the open pages are the services provided by the organization. The multiple framework strategies are working on controlling the critical path associated with the security mechanism associated with the organization. The frameworks are associated in providing increased level of defense, prevention from the threats, risk maturity, and recovery from the attack. The stages which are associated with the framework are summarized as Risk awareness focuses on the automation of the governance process and risk associated with the development of instruments and risk management is the process of handling the risk by the integration of the governance and security operations which are associated with the system.
“Network security protocols for example, Wi-Fi protected access 2 should be used for securing the network for the wireless connectivity framework” (Raghuwanshi, 2014). The public key infrastructure is used for providing peer to peer consultation and implementation of the services. To check the security issues it is necessary to list out all the security issues which are associated with an application. The next step is to identify the sub parameters of the issues. “All the sub parameters should be tested separately. The attribute based access control is used for mitigating from the security risk associated with the data connection and the devices” (David, 2013). It should be implemented on peer to peer controlling of devices, network, and the data. “The designing of the architecture should give the clear perspective view of the security controls and postures, new security application can be developed, and the existing application can be implemented by the security model” (Michigan, 2014). The security concern should follow the following key fields:
The security concern can be raised in the implementation and operation of organizational activities in the summarized manner:
Security is main concern for any organization. The security system can be categorized in the four main categories which are summarized below:
The table below gives the detail of new business model with the improved version of security:
| Industry | Services or solution offered | Sensors or devices used | Analytics | Interfaces | Result |
| Utilities | Real time collection of the data should be done Prediction for the demand and supply | Energy, water and the gas meter can be used | Prediction of the usage and demand and supply | Any internet can be used for accessing | Consumers can focus on cost saving |
| Manufacturing | Remote monitoring Automation in the production line | Data acquisition and supervisory control | Detection of the anomaly in the devices
Predictive Maintenance | Mobile terminals can be used for connection with the remote consultation | Improved efficiency of the operation |
| Health care | Real time collection of the data should be done Management of chronic disease | Mobile phones and personal medical devices | Detection of the anomaly in the medical data | Tele consultation with the remote specialist | Improvement in the health of the patient at lower cost. |
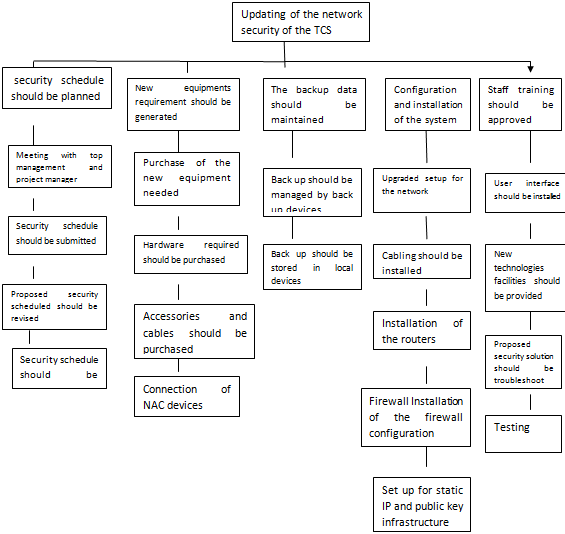
Tata consultancy service is an organization which offers IT services, consultation and strategies to the enterprise for making it a global organization. It provides the platform to the services and infrastructure for the world of IT technology. For the implementation of smart services it is important periodically physical checks should be done and the devices which are providing gateway to the vulnerabilities and attacks should be replaced. When dealing with the security concern of the organization, the preventive steps should be taken of two things which can be categorized as violation of information and unauthorized accessing of the information. The data leakages and breaches should be prevented by ensuring effective identification of the data owner. Data security and privacy is the collection of encryption technologies or procedures, prevention from the data leakage, and services offered for key management. In this paper, we focus on improving the security concern of the Tata consultancy services.
Singh, A. (2013). A Parametric Approach for Security Testing of Internet Applications. 1st ed. [ebook] Available at: https://www.infosys.com/it-services/validation-solutions/white-papers/documents/security-testing-internet.pdf [Accessed 14 Aug. 2016].
NelsonHall, F. (2015). IT outsourcing vendor profile of TCS managed security services. 1st ed. [ebook] Available at: http://www.tcs.com/SiteCollectionDocuments/Analyst%20Reports/NelsonHall-TCS-MSS-0915-1.pdf [Accessed 14 Aug. 2016].
Muruthy, N. (2008). TCS Sustainability Report. 1st ed. [ebook] Available at: https://www.infosys.com/sustainability/Documents/infosys-sustainability-report-0809.pdf [Accessed 14 Aug. 2016].
Buhalis, S. (2014). TCS Code of Conduct and Ethics. 1st ed. [ebook] Available at: https://www.infosys.com/investors/corporate-governance/Documents/CodeofConduct.pdf [Accessed 14 Aug. 2016].
Dewanjee, R. (2010). TCS Annual report. 1st ed. [ebook] Available at: https://www.infosys.com/investors/reports-filings/annual-report/annual/Documents/Infosys-AR-05.pdf [Accessed 14 Aug. 2016].
Oshri, I. (2011). Managing Dispersed Expertise in IT offshore Outsourcing: from tata consultancy services. 1st ed. [ebook] Available at: http://www.juliakotlarsky.com/MISQExecutiveOshriKotlarskyWillcocks2007.pdf [Accessed 14 Aug. 2016].
Bhatia, R. (2013). Grid Computing and Security Issues. 1st ed. [ebook] Available at: http://www.ijsrp.org/research-paper-0813/ijsrp-p2094.pdf [Accessed 14 Aug. 2016].
Turn, R. (2009). Privacy and security issues in information system. 1st ed. [ebook] Available at: https://www.rand.org/content/dam/rand/pubs/papers/2008/P5684.pdf [Accessed 14 Aug. 2016].
Kunnauthur, A. (2008). Information Security Issues In Global Supply Chain. 1st ed. [ebook] Available at: http://www.utoledo.edu/business/ISCMIA/documents/IS_Issues_In_Global_SCM_Draft_.pdf [Accessed 14 Aug. 2016].
Dhawale, F. (2013). Document Security and Compliance Enterprise Challenges and Opportunities. 1st ed. [ebook] Info trends. Available at: http://www.nuance.com/ucmprod/groups/imaging/@web-enus/documents/collateral/nc_027979.pdf [Accessed 14 Aug. 2016].
Maheshwari, R. (2014). Tata Consultancy Services. [Blog] Money Control. Available at: http://www.moneycontrol.com/competition/tataconsultancyservices/comparison/TCS [Accessed 14 Aug. 2016].
Murugappan, M. (2015). Leveraging CMMI framework for engineering services. 1st ed. [ebook] Available at: http://www.tcs.com/SiteCollectionDocuments/White%20Papers/EIS_Whitepaper_Leveraging_CMMI_Framework_Engineering_Services_0212-1.pdf [Accessed 14 Aug. 2016].
Raghuwanshi, K. (2014). Privacy and Cyber Security Emphasizing privacy protection in cyber security activities. 1st ed. [ebook] Available at: https://www.priv.gc.ca/information/research-recherche/2014/cs_201412_e.pdf [Accessed 14 Aug. 2016].
Butt, D. (2014). erprise security and risk management solution and services. 1st ed. [ebook] Available at: http://www.tcs.com/SiteCollectionDocuments/Brochures/ESRM-0914-1.pdf [Accessed 14 Aug. 2016].
Kulandaivel, P. (2013). Design strategy for hardware accelerators for wireless broadband systems. 1st ed. [ebook] Available at: http://www.tcs.com/SiteCollectionDocuments/White%20Papers/EIS_Whitepaper_Design-Strategies-of-Hardware-Accelerators-for-wireless-broadband_11_2009.pdf [Accessed 14 Aug. 2016].
Michigan, P. (2014). Information Security Plan. 1st ed. [ebook] Available at: http://www.security.mtu.edu/policies-procedures/information-security-plan.pdf [Accessed 14 Aug. 2016].
Daya, B. (2014). Network Security: History, Importance, and Future. 1st ed. [ebook] Available at: http://web.mit.edu/~bdaya/www/Network%20Security.pdf [Accessed 16 Aug. 2016].
Hutchings, A. (2012). Computer security threats faced by small businesses in Australia. 1st ed. [ebook] Available at: http://aic.gov.au/media_library/publications/tandi_pdf/tandi433.pdf [Accessed 16 Aug. 2016].
David, J. (2013). Cyber security and fraud: The impact on small businesses. 1st ed. [ebook] Available at: http://www.fsb.org.uk/docs/default-source/fsb-org-uk/policy/assets/publications/fsb_cyber_security_and_fraud_paper_final.pdf?sfvrsn=0 [Accessed 16 Aug. 2016].
She, W. (2007). Security For enterprise resource planning. 1st ed. [ebook] Available at: https://www.utdallas.edu/~bxt043000/Publications/Technical-Reports/UTDCS-33-07.pdf [Accessed 16 Aug. 2016].
Appari, A. (2010). Information security and privacy in healthcare: current state of research. 1st ed. [ebook] Available at: http://www.ists.dartmouth.edu/library/501.pdf [Accessed 16 Aug. 2016].
Michael, A. (2014). Cisco IoT System Security: Mitigate Risk, Simplify Compliance, and Build Trust. 1st ed. [ebook] Available at: http://www.cisco.com/c/dam/en/us/products/collateral/se/internet-of-things/iot-system-security-wp.pdf [Accessed 16 Aug. 2016].
Gordon, J. (2013). Business Opportunities in the Security Industry New paths to success in a changing market. 1st ed. [ebook] Available at: http://Business Opportunities in the Security Industry New paths to success in a changing market [Accessed 16 Aug. 2016].
Ristov, S. (2014). C LOUD C Omputing S Ecurity In B Usiness I Nformation S Ystems. 1st ed. [ebook] Available at: https://arxiv.org/ftp/arxiv/papers/1204/1204.1140.pdf [Accessed 16 Aug. 2016].
Bob, H. (2016). Cyber security: Planning Guide. 1st ed. [ebook] Available at: https://transition.fcc.gov/cyber/cyberplanner.pdf [Accessed 16 Aug. 2016].
MyAssignmentHelp.co.uk is not a new name in the field of essay writing services. For almost a decade MyAssignmentHelp.co.uk has provided the students in the UK with the essential essay help whenever requested and still continues to do so with the same enthusiasm. In fact, their custom essay writing help is specially designed to serve the specific requirements of every student in the country.
Upload your Assignment and improve Your Grade
Boost Grades