Bonanza Offer FLAT 20% off & $20 sign up bonus Order Now
NSW Government is a massive body that is home to a number of operations, activities and components. There is a huge workforce that is employed with NSW Government and the tools and equipment that are used across the body is also huge in number. It is because of the presence of multiple entities in terms of man and machine that the NSW Government is exposed to a lot many security risks. The report covers the security risk diagram for NSW government along with the description of each risk. Some of these risks are deliberate and there are a few that occur by accident and the same has been highlighted in the document along with the comparison between the risks and uncertainties. There are also issues that appear during the implementation of the security policy which has been covered in the report as well along with the list of security measures.
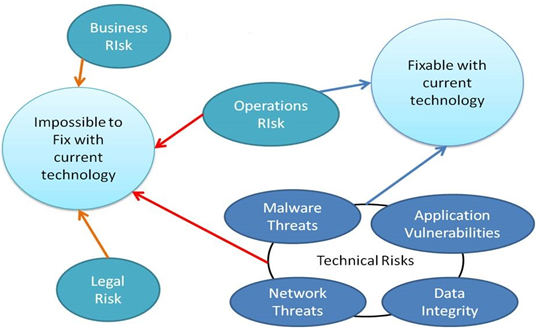
The information that is associated with the NSW Government and all of its components is of several information types. It includes the information that is only for official use, private information, sensitive information, public information and many more. The risks that have been illustrated in the diagram drawn above have got varying degree of impact and the primary factor behind the same is the type of the information that the risk affects.
Integrity of the data or the information is violated when there are unauthorized modifications done on the same. There are a number of integrity risks that take place which attempt at altering the information or the medium through an unauthorized manner which causes severe impact.
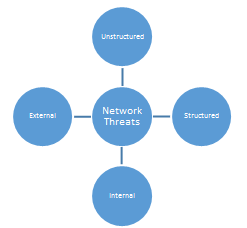
NSW Government is also exposed to a number of network threats. These threats are classified in various categories on the basis of network location and the type of the threat as displayed in the diagram above (etutorials.org, 2016).
Some of the examples of these threats include man in the middle attack, denial of service, and distributed denial of service, sniffing and likewise (hubpages.com, 2016).
There are a lot many malware that are present in the technological world and newer types are being created on a frequent basis. These malware have the potential to impact the system in a critical manner by violating the properties of the information that is associated with the same (www.us-cert.gov, 2016).
The vulnerabilities that are associated with several numbers of applications that are present in the architecture of NSW Government are endless. These may include the attacks relating to account hijacking and APIs.
These risks occur due to the fault at the end of the man or machine involved in a particular activity. The major causes of these risks include the negligence or inadequate knowledge of the professional that is involved in an activity (www.finance.nsw.gov.au, 2016).
The market trends and the rules of the business keep on changing from time to time. The same leads to a number of risks that may result in loss or minimization of profits.
With the presence of so many entities, the operations of NSW Government are bound by a lot many legal policies. There are also risks associated with these as the same can be violated deliberately or by mistake.
| Risk ID | Risk | Likelihood | Impact | Risk Ranking |
| RS-1 | Data Integrity | M | H | H |
| RS-2 | Network Threats | H | H | H |
| RS-3 | Malware Threats | M | M | M |
| RS-4 | Application Vulnerabilities | H | M | M |
| RS-5 | Operations Risks | M | M | M |
| RS-6 | Business Risks | L | H | H |
| RS-7 | Legal Risks | L | H | H |
| Deliberate Risks | Accidental Risks |
| These are the category of risks that are executed due to malicious intent and are well planned in nature as they are done out of deliberate action (Vavoulas, 2016). | These are the category of risks that happen by chance or by mistake. |
| The impact can be severe as there is extensive planning done behind these risks. | The impact can vary from low to high. |
| Data integrity risks, malware attacks and networks threats are deliberate risks. Legal and operational risks can be deliberate in some cases. | Application vulnerabilities and business risks are often accidental (searchsecurity.techtarget.com, 2016). Legal and operational risks can be accidental in some cases. |
| Challenge | Description |
| Human Factors | With the presence of a vast number of human entities both internal and external to NSW Government, there may be human factors that may prove to be a hurdle in the implementation process. There may be scenarios wherein the communication gaps may exist or a dispute may occur between the two parties. |
| Organizational Factors | These are the factors that are present at various organizational levels in the NSW Government such as senior level officials, middle level managers, workers and likewise. |
| Technological Factors | Technology can be a boon as well as curse in various cases. There may be technological conditions such as compatibility issues, obsolete technology and likewise that may cause problems during the implementation process. |
The risks that are associated with the NSW Government have been discussed in the report in the sections above. These risks can be measured in advance and control measures can also be designed as per the prediction and analysis. The control can take place by various risk treatment strategies such as avoidance, mitigation, transfer and likewise. However, uncertainties are the events that cannot be predicted and hence can never be measured. There are no control strategies that can be devised for the uncertainties that are associated with the system (Surbhi, 2016).
The impact that is caused by the risk and uncertainties can also vary as the formal will always result in a negative impact whereas the latter may have a positive or a negative impact as well. The uncertainties that are associated with NSW Government can be in the form of market trends or natural disasters and hazards.
The security policy that is designed for NSW Government must have the measures of recovery in the scenario of a disaster. These measures shall always make sure that the data and information is stored in the form of back up and can be easily retrieved in case of an attack.
Network monitoring, network scans and intrusion detection systems are some of the network controls that can be installed in order to protect the network attacks from taking place.
There are also a number of malware controls that can be implemented in the form of anti viruses and anti malware software to stay protected from all the types of malware. Also, the latest internet security software and tools must also be installed in all the systems to stay protected from all the web based malware attacks.
It is necessary to adhere to the legal and regulatory policies at all times to make sure that one hundred percent compliance is achieved. A legal team can be deployed by the NSW Government to deal with all of the legal activities that are associated with the NSW Government.
Identity and access management must also be of supreme nature and quality so that the same becomes difficult for the intruder and the attacker to break in. NSW Government must also make sure that the physical security that is set up across all the entry and exit points is never compromised. There should be use of multi layer authentication system and stronger passwords along with one time passwords and single sign on.
NSW Government is a big body that is formed of a number of small, medium and big components in the form of workforce, external stakeholders, applications, operations, tools, equipment, policies and many others. All of these entities work together as a single unit to achieve the objectives of the NSW Government. Due to the presence of such varied entities, there are a number of security risks that come up in front of the NSW Government. These risks can be deliberate as well as accidental in nature on the basis of the motive behind the same. There are also many uncertainties that are associated with the NSW Government that cannot be measured in advance unlike the risks. There are a number of measures that can be adopted to deal with these risks in the form of controls and improved policies. However, there can be many challenges that may come up during the implementation procedure in the form of human, technological and organizational factors. These challenges can be tackled with proper management policies and through the application of accurate and required techniques.
Etutorials.org,. (2016). The Four Primary Types of Network Threats :: Chapter 1: Understanding Network Security Threats :: Part I: Introduction to Network Security :: CCSP Cisco Certified Security Professional Certification :: Networking :: eTutorials.org. Etutorials.org. Retrieved 27 August 2016, from http://etutorials.org/Networking/Cisco+Certified+Security+Professional+Certification/Part+I+Introduction+to+Network+Security/Chapter+1+Understanding+Network+Security+Threats/The+Four+Primary+Types+of+Network+Threats/
hubpages.com,. (2016). Different Types of Network Attacks And Security Threats and Counter Measures. HubPages. Retrieved 27 August 2016, from http://hubpages.com/technology/Types-of-Network-Attacks
searchsecurity.techtarget.com,. (2016). Accidental insider threats and four ways to prevent them. SearchSecurity. Retrieved 27 August 2016, from http://searchsecurity.techtarget.com/tip/Accidental-insider-threats-and-four-ways-to-prevent-them
Surbhi, S. (2016). Difference Between Risk and Uncertainty - Key Differences. Key Differences. Retrieved 27 August 2016, from http://keydifferences.com/difference-between-risk-and-uncertainty.html
Vavoulas, N. (2016). A Quantitative Risk Analysis Approach for Deliberate Threats. Retrieved 27 August 2016, from http://cgi.di.uoa.gr/~xenakis/Published/39-CRITIS-2010/CRITIS2010-RiskAnalysisDeliberateThreats.pdf
amsro.com.au,. (2016). Information Technology and Security Risk Management Top 12 Risks What are the risks? What are the solutions?. Retrieved 27 August 2016, from http://www.amsro.com.au/amsroresp/wp-content/uploads/2010/12/AMSRO-TOP-12-Information-Technology-Security-Risk-Management-1.pdf
finance.nsw.gov.au,. (2016). NSW Government Digital Information Security Policy | NSW ICT STRATEGY. Finance.nsw.gov.au. Retrieved 27 August 2016, from https://www.finance.nsw.gov.au/ict/resources/nsw-government-digital-information-security-policy
praxiom.com,. (2016). ISO IEC 27000 2014 Information Security Definitions. Praxiom.com. Retrieved 27 August 2016, from http://www.praxiom.com/iso-27000-definitions.htm
us-cert.gov,. (2016). Malware Threats and Mitigation Strategies. Retrieved 27 August 2016, from https://www.us-cert.gov/sites/default/files/publications/malware-threats-mitigation.pdf
MyAssignmentHelp.co.uk is one of the leading academic solution providers in the United Kingdom which has assisted a countless number of students to achieve their academic goals with unmatched academic writing help. With the proficient academic writing services from our expert writers, you won’t have to worry about those stringent deadlines, complicated essay topics, or clashing assignments anymore.
Upload your Assignment and improve Your Grade
Boost Grades